Security overview - Azure Arc
Security gaps often emerge when managing infrastructure across public cloud, private cloud, and on-prem environments. Azure Arc helps bridge those gaps by extending Azure security tools to Arc-enabled servers running anywhere. Read this Microsoft Learn article to see how it works and how your organization can benefit. Contact ITontology for a complimentary security assessment of your hybrid environment.
What is the shared responsibility model for Azure Arc-enabled servers?
The security of Azure Arc-enabled servers is a shared responsibility. Microsoft is responsible for securing the cloud service that stores system metadata, protecting privacy, documenting optional security features, publishing regular agent updates, managing RBAC access, and securing the server infrastructure. Users are responsible for securing the server itself, managing credentials, determining the application of security features, and ensuring compliance with legal and internal policies.
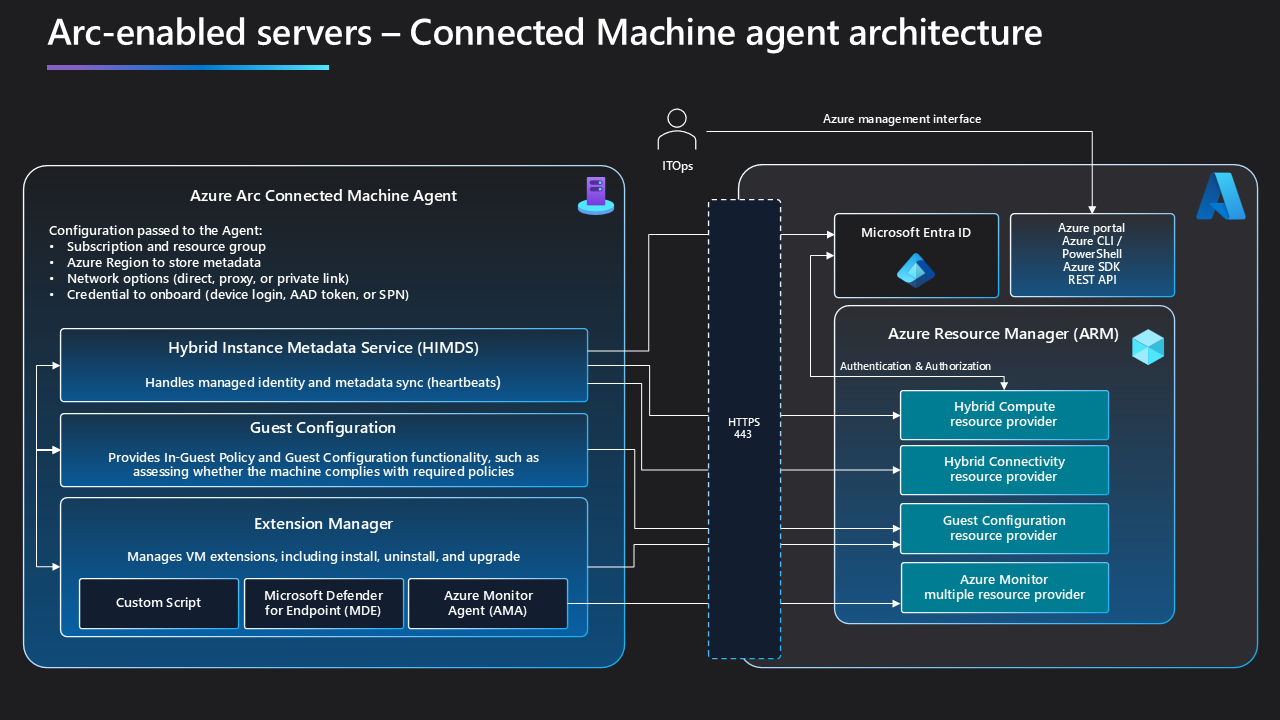
How does the Azure Connected Machine agent function?
The Azure Connected Machine agent acts as an enablement platform that connects your machine to Azure. It establishes a relationship with your Azure subscription, provides a managed identity for authentication, enables additional capabilities through extensions, and enforces settings on your server. The agent is essential for relaying data and actions between your managed server and Azure.
What security measures should be taken for Tier 0 assets?
For Tier 0 assets, it is recommended to use a dedicated Azure subscription to minimize access and closely monitor permissions. You should also disable unnecessary management features, such as remote access capabilities and the extension manager, unless they are needed. Implementing an extension allowlist can help restrict the use of extensions to only those that meet your security requirements.
Security overview - Azure Arc
published by ITontology
In our cloud-first, mobile-first world, we are absolutely focused on empowering everyone within the organization. Hardware and software play a significant role in every company, but the primary focus has shifted to employees. Identity and conditional access are at the foundation of data protection, but collaboration is necessary in the Modern Workplace. Low level IT tasks are gone, and budgets have been refocused on securing and protecting data on every device from every location. Organizations that must meet certain compliance requirements have an extra layer of responsibility and accountability.
ITontology was founded to solve these challenges. In our cloud-first, mobile-first world the challenges can be overwhelming. Not to worry, our team and experience will guide you through the digital transformation process and empower everyone within your organization. Our vision, experience and powered 100% by Microsoft will provide best in class technology solutions. The best part, it’s all right at our fingertips and deployment can be automated from the cloud. The technology, security, value, and expense are finally all aligned. The time is now, and we are here to help, so let’s get to work on your digital transformation and turn your business into a Modern Workplace.





